Email is an essential part of digital marketing and organizational communication. It has carved its niche and earned its place in customers’ hearts. It lies at the core of various operations across multiple devices and environments.
With over 4 billion active email users worldwide as of 2024, email marketing opens golden sales opportunities for companies and, unfortunately, represents a large attack surface. It has been a constant target for cyber-attacks since its introduction. And the situation is getting worse with each year. Just consider the recent statistics:
- Almost 60% of organizations suffer from phishing attempts on a weekly or daily basis.
- There are over 3 billion phishing emails sent each day.
- 35% of ransomware attacks come through email.
- Cyber-attacks cost companies across the World a loss of billions of dollars.
The research indicates a disturbing uptick in email-based cyber threats. There is a startling rise in phishing expeditions, divulging sensitive information, Business Email Compromise (BEC) schemes, and all sorts of sophisticated and even AI-powered frauds.
The threat is real and growing. Today’s continuously evolving landscape of cyber threats brings the urgency of robust email security measures into the spotlight and intensifies their importance. Whether you are a small startup or an industry leader, combating these threats is your top priority.
The good news is that you are not alone. There are time-proven instruments to strengthen your email security. Email authentication is one of them. It is a critical defense mechanism for email channels, which involves several regularly updated protocols to create a safe environment.
Let’s dive into the definition and the importance of introducing this defense mechanism in your email marketing and consider email authentication best practices.
What Is Email Authentication?
Email authentication refers to technical solutions and standards for inspecting and verifying digital correspondence. It is a multi-step process that validates the legitimacy and integrity of the sender’s source and the technical side of the message.
Email authentication allows the receiving mail server to determine three crucial criteria: whether the digital newsletter comes from a trustworthy source, whether the message is from the person specified in the “From” field, and whether the email was altered during transit.
In practice, companies use technical standards to make verification possible. They introduce certain settings in their DNS servers to supplement SMTP, and help mail servers decide what to do with incoming digital correspondence. Five key standards make up email authentication. Let’s consider them closer.
Types of Email Authentication
Email authentication has several time-proven, widely adopted standards: SPF, DKIM, DMARC, ARC, and BIMI. If they are missing or incorrectly set up, the receiving mail server raises a red flag and considers email cautiously. Get a basic understanding of each to see how they help fight cyber threats and secure a healthy environment in the email channel.
SPF
Sender Policy Framework is among the most popular, well-recognized, and widely adopted email authentication standards. It is a complex and powerful mechanism that pioneered domain-based validations.
The main purpose of SPF is to verify the sender of the digital newsletter. It provides email marketers, organizations, and domain owners with instruments to publish a list of specific IP addresses or sources allowed to send mail from their names.
When the message is sent, the IP of the sending host is put in the Return-Path address. The receiving mail server looks up the authorized sending sources for that IP. If it is on an allowlist, then the message is validated. Otherwise, SPF authentication is not passed, and a red flag is raised.
DKIM
DomainKeys Identified Mail is another popular email authentication standard that many companies introduce in their email channels to make them safe. It ensures the email body content has not altered in transit.
DKIM makes the most out of cryptography. It generates secured public and private key pairs for each message. The private key encodes the message headers and creates a unique signature hash that is added to the message headers. Only ESP or signing authority knows the private key.
The public key related to the private key is stored in the domain’s DNS. It is accessible to the receiving server to verify the signature by decoding the hash. If decoding is successful, then the signing domain takes responsibility for that content so it can be trusted. Otherwise, the message could be corrupted.
DMARC
Domain-based Message Authentication, Reporting, and Conformance is the third most popular email authentication protocol that fights email spoofing. It builds on the work of two previous standards, SPF and DKIM, uniting them into a common framework and ipso facto reinforcing their security measures. In essence, it matches what these standards validate with the header that the end user receives and ensures the domain in the “Form” field is verified.
The best part is that DMARC allows owners to set a policy for messages that fail to authenticate in their DNS. It features instructions on what the receiving mail server should do with messages.
On top of that, the receiving server generates a report and sends it back to the sender (domain owner), informing about messages that have successfully passed or failed authentication checks. That offers companies the necessary knowledge to improve their security measures next time.
The only drawback is that DMARC is considered successful if one of the protocols (SPF or DKIM) passes.
ARC
The Authenticated Received Chain protocol is a lesser-known and less-adopted email authentication standard. Nevertheless, it is a highly recommended addition to SPF, DKIM, and DMARC. It provides an extra layer of security to amplify safety in the email channel by addressing possible insecurities with indirect mail flow.
ARC was designed to preserve email authentication across multiple hops by sealing email authentication results of email intermediaries (mailing lists or account forwarding) that forward a message to its final destination, thereby verifying its identity or exposing intruders.
It has three main components: the ARC Authentication-Results header that contains results of SPF, DKIM, and DMARC checks; the ARC Message Signature header that contains a snapshot of critical data of the digital newsletter such as the content of “to,” “from,” “subject,” and body; and, ARC Seal header with crucial header information.
The receiving server checks the ARC result and the DMARC to ensure the legitimacy of the forwarded emails.
BIMI
Brand Indicators for Message Identification are an underdog of email authentication standards that companies often neglect. Although they do not act as a traditional technical solution for verification, they still contribute to the safety of the email channel through traditional visual confirmation.
BIMI provides senders or domain owners with simple instruments to specify branded imagery, which appears alongside authenticated messages. Some email clients display it as the user photo, while others show it as the sender’s initials. Humans can recognize it as a visual cue of authenticity without extra effort.

Email authentication – visual snippet from infographic “SPF, DKIM and DMARC Explained” by Inboxally
How Does Email Authentication Work?
SPF, DKIM, DMARC, ARC, and BIMI may sound tricky due to their acronym nature and technical origin. However, they are pretty straightforward in what they do. Here is the basic scenario of email authentication at work
Step 1—The email sender (organization or domain owner) introduces security measures through protocols. They typically authenticate IP addresses with SPF, configure DKIM signatures for messages, protect the domain with DMARC authentication, publish BIMI records, and enable ARC messages by letting servers sign ARC headers.
Step 2—The receiving mail server initiates an email authentication check-up. It retrieves the technical data and reviews details about an incoming email message, comparing them against the rules defined by the domain owner.
In general, it verifies email using SPF and DKIM protocols. If none of them passes, then it applies to DMARC policy. If at least one of them turns out to be valid, the mail server decides on its fate. It may deliver, flag, place it in the spam folder, or even reject the message. If DMARC is specified correctly, it also generates a report and sends it to the owner of the digital newsletter.
If ARC is set up correctly, it also initiates the check-up for this factor that may alter the decision about the message destiny.
Reasons for Introducing Email Authentication
Companies are highly advised to introduce email authentication in their email marketing because Simple Mail Transfer Protocol (SMTP) has no built-in authentication protocols. It was designed to transfer messages, not protect them from hackers. It cannot fight cyber-attacks, leaving the channel open for threats. Therefore, it is critical to implement separate measures and improve them with email authentication best practices and up-to-date solutions.
Another good reason is that you need to authenticate your emails to reach Gmail and Yahoo subscribers in your list. Last year, Gmail and Yahoo announced new rules for all senders, “regular” and “bulk.” Both mail clients require every sender to ensure email security with authentication protocols (DKIM, SPF, DMARC). Maintaining a low spam complaint rate and tracking the sender’s reputation are highly recommended.
Establishing trust between senders and recipients is another reason to introduce email authentication in the routine. Companies that follow proper email verification protocols guarantee their identity is verified. They also ensure confidentiality, integrity, and availability of messages. That could not help but build trust with subscribers and demonstrate their social-conscious positions.
On the other hand, adopting email authentication protocols signals to mailbox providers that emails are legitimate and that companies are responsible, lawful, and reliable players in the arena that respect their recipients. That may overcome some blocks on their path to inboxes. Plus, with properly configured DMARC and ARC, they get valid aid for troubleshooting and analyzing email flows.
There is more. When introducing email authentication, companies take their communication with customers to a new level by unlocking the potential of a safe place and uninterrupted communication. That leads to some extra bonuses that translate into true benefits for the company. This includes
- Reduced email bounces and spam rates.
- Enhanced deliverability rate.
- High sender’s reputation.
- Protection from blacklisting.
- Improved key email metrics such as open and click-through rates that maximize campaign ROI.
- Reinforced customer relationships.
- Increased trust and confidence in communication with subscribers.
- Heightened company’s credibility and better customer engagement.
- Compliance with industry standards to avoid potential legal and regulatory issues and fines.
Finally, it is crucial to note that setting up safety protocols is one thing, but introducing email authentication best practices is another. Following the most up-to-date professional recommendations plays a pivotal role in successfully facing the ever-evolving landscape of cyber threats, mitigating consequences more efficiently, and making the company proactive in its fight for a safe email channel. Let’s consider the best tips from security organizations and specialists to give you a strategic advantage.

Importance of email authentication – visual snippet from infographic “SPF, DKIM and DMARC Explained” by Inboxally
But first things first – how do you check your email authentication status to identify areas for improvement?
How to Check Your Email Authentication Status?
The simplest way to check your email authentication status is to send an email to yourself. Choose the domain you want to test and hit the button. After receiving a newsletter, look for SPF, DKIM, and DMARC mentions in the message header.
For instance, Gmail provides a well-formatted table where you can inspect all vital fields: “From,” “To,” “SPF,” “DKIM,” and “DMARC.” Plus, the BIMI record (the brand logo) is displayed next to the email message in the list. All you need to do is open the Gmail web app, click on your message, press the ‘more’ button next to the ‘reply’ icon, and choose “show original.”
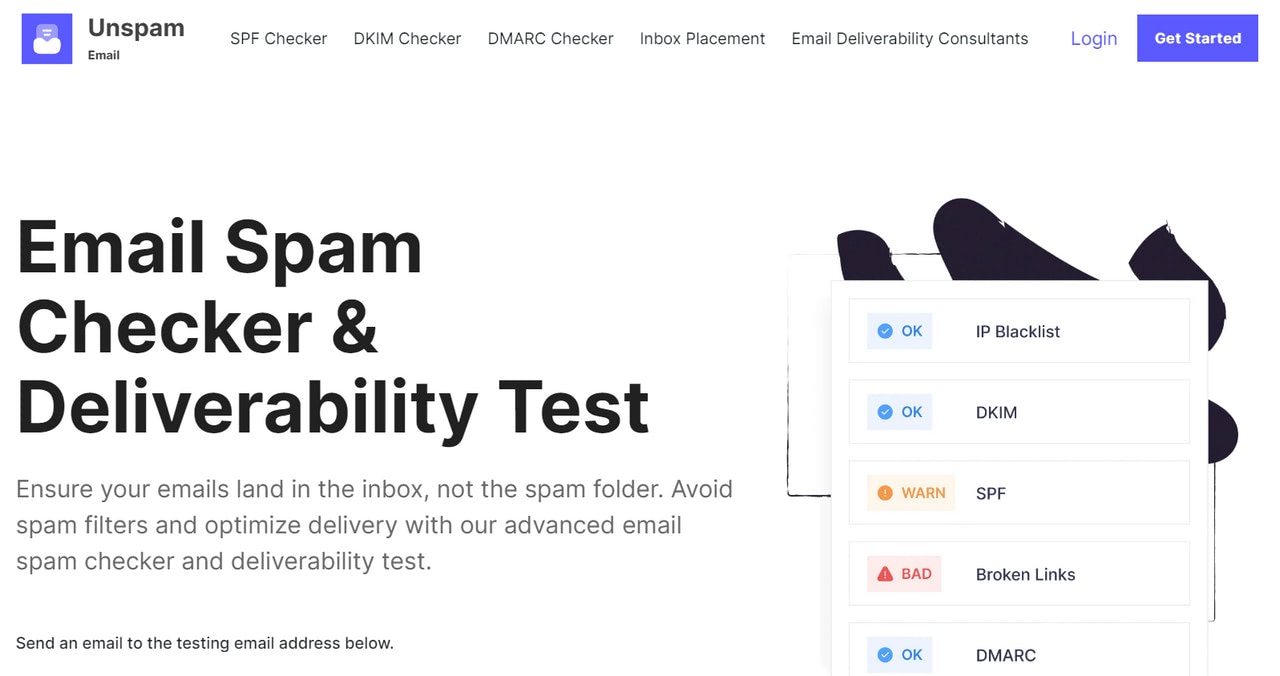
What if you need a quicker and handier way to test your email authentication or identify issues that cause DMARC failures? The best solution is to use a dedicated monitoring tool like Unspam.
Unspam is the leading instrument in the niche. It is the simplest, quickest, and easiest way to check email authentication status and spot inconsistencies beforehand. It has handy tools to check the validity and correctness of SPF, DKIM, and DMARC records.
Just send the email to the specified account. The platform inspects the newsletter, generates a report, and delivers information in digestible form so that any non-tech-savvy person can identify the possible root of the problem. In addition, it provides actionable guidance and professional insights on resolving problems and getting your emails back in the inbox.
With a skilled and experienced team of email deliverability consultants, Unspam gives you all the tools to check email authentication and ensure security in your digital communication with subscribers.
Alternatively, you may try online tools like DMARC Record Checker. Although they will not provide you with insights and helpful aids like Unspam, they could become a starting point for authentication checks.
Email Authentication Best Practices
Email authentication best practices ensure optimal functionality of the technical side of the email channel and guarantee up-to-date email security that efficiently protects from cyber threats. We have gathered the best tips in the niche, breaking them into several categories. Let’s start with the general practices.
The General Practices
The general practices for improved email authentication are:
Introduce all security protocols. Although the global adoption of BIMI and ARC are pretty low, they still provide protection. Therefore, introduce all standards in your routine without exceptions.
Stay away from blacklists.
Maintain a high sender’s reputation.
Use only a dedicated server.
Use encrypted connections.
Use Unspam to check email authentication regularly and simulate email delivery to determine possible weaknesses in your infrastructure.
Inspect the health of your technical environment and improve it with professional security software.
Use a consistent sender address and name. Make them branded.
Do a test run of SPF and DMARC records with hard fails.
Assign a PTR record for any IP address you use to send emails.
Use short Time-to-Live (TTL) values for your DNS records.
Monitor DMARC reports, address issues, and adapt SPF and DKIM accordingly.
Review and update your DNS records regularly. Ensure SPF, DKIM, and DMARC records are up-to-date. This is especially important when your email service provider introduces changes or you alter your email infrastructure.
Ensure third-party services are properly authenticated.
Scale email authentication across all systems and departments.
Meet regulations and practices in other regions if you own a multinational organization or serve customers outside your country.
Balance strict authentication policies with usability. As DMARC may cause rejection of even legitimate emails, it is vital to test and monitor it to keep your email campaign from unfortunate failures.
Track the organization’s email activity by monitoring who sends and receives emails.
Provide educational opportunities for your employees to learn the best email security practices.
SPF
As the protocol restricts IPs that can send emails from your domain, it is the first layer of defense to fight spoofing. Follow these tips to ensure it is formidable:
Publish SPF records for MAIL, FROM, and EHLO domains. They should be aligned with the latest standards.
Keep your SPF records as specific, simple, and clean as possible. Do not overcrowd them with multiple hosts, nor permit more IPS than necessary. Instead of authorizing every source, clean up the list and choose only those critical for your infrastructure.
Create a single universal SPF record for multiple domains in the same infrastructure. However, use as few “include:” directives as possible and avoid nested instances.
Never use the “+all” mechanism. Allowing any sender to deliver messages on your behalf makes SPF useless. As malicious actors may easily break your server and domain, you may become a host to malicious activity involuntarily. The only way to use “all” is in the “-all” or “~all” mechanisms.
Keep ranges of CIDR notation in SPF records between /30 and /16. Everything below may compel receivers to discount or ignore your records.
Publish “-all” on your domains that do not send emails from you or are currently “parked.”
Before sending emails, check whether all your active domains are included in the SPF record.
DKIM
Proving ownership of a message through an encoded signature, DKIM comes as the second layer of protection. Follow these tips to configure it properly and minimize its weak spots.
Ensure the DNS server can support long text records such as EDNS0 or TCP-based record fetches.
Make DKIM keys at least 2048 bits long. Although the 1024-bit length is widely adopted, the longer DKIM keys you have, the more challenging it is for malicious actors to break. Plus, everything less than 1024-bit is completely ignored by the receiving side.
Rotate your cryptographic DKIM keys regularly. If you send sensitive data or millions of emails monthly, changing the keys at least once or twice a year is advisable.
Add two signatures to a sensitive email with two different selectors. If one of your keys is compromised, another ensures the email passes the DKIM check.
Do not use a single key for all your customers. As a rule, companies that use ESP preach these ways. The rule of thumb is to assign a unique key for each client. Ask your ESP team to introduce this practice.
Use DKIM keys that are compatible with the recipient’s mail server.
Sign your bounce messages with DKIM.
DMARC
Uniting SPF and DKIM into a framework and providing a reporting mechanism, DMARC reinforces core email authentication protocols and serves as extra protection. Here are some professional tips to unlock its potential:
Get the most out of the DMARC reporting mechanism. Use professional tools to translate XML files into easily understandable language. This way, you may analyze them more efficiently and get more thorough insights into your email channel health.
Ensure every email has an identifier alignment. This adds a layer of protection, makes the email look more legitimate, and increases its trust, passing the receiver’s security mechanisms.
Do a test run of DMARC with quarantine and reject settings.
Follow the regular DMARC enforcement route gradually but steadily. Begin with “p=none” to receive reports about all your sending sources. Escalate your policy to quarantine or rejection only if you successfully pass the monitoring stage.
Protect domains and subdomains without traffic. “Parked” domains are a prime target for hackers since they get less attention from companies. Therefore, they can be easily spoofed and used for malicious activity. By configuring DMARC for inactive domains, you may catch cyber-attacks from your server and deal with the situation immediately.
ARC
Adding a layer of protection for indirect mailflows, ARC may be the last thing to remember. However, it preserves authentication across multiple hops and adds a certain security value. As a company that wants to expand its client reach through subscribers’ friends and colleagues, it is a crucial standard to introduce. Here are some professional tips to implement:
- Use it with popular authentication mechanisms such as SPF, DKIM, or DMARC.
- Change ARC keys periodically.
- Approve only intermediaries you trust.
- Limit ARC signers.
- Check reports regularly to identify possible issues.
BIMI
Although BIMI is still in the beta stage, it has received good feedback from Gmail, Fastmail, Yahoo, AOL, and even Apple, which tested this feature to see how it impacted security. Plus, it involves people in a routine of making the email channel secure, transparent, and healthy. So, you should certainly adopt this security measure.
The best advice is to introduce this security standard by following all its crucial steps, which entail several steps.
First, you must obtain a Verified Mark Certificate, which is additional proof of domain ownership. This includes acquiring an Extended Validation certificate and proving the right to use a trademark registered in a competent jurisdiction.
Second, when choosing the logo for the BIMI record, ensure it matches the trademark. It should also meet basic technical criteria. This involves making it square, placing it against a transparent background, and presenting it in SVG format. It must also be small and lightweight, less than 32kb.
Third, prove that your company is a domain name registrant.
Fourth, do the previous steps for each instance if you have multiple domains and logos.
Fifth, publish a BIMI record for your domain in the DNS.
Sixth, use BIMI Inspector to validate or create your BIMI record.
Finally, maintain a good domain and IP reputation. Use Unspam to check these factors and learn how to improve them.
Last but not least
Implementing email authentication best practices requires companies to identify the technical support personnel responsible for the routine. They should create a comprehensive email security strategy and document each step to have a solid ground for solving possible issues.
In addition, members of the technical squad should have a plan to act in emergencies. For example, if one of the key pairs is compromised, a team should initiate unscheduled key rotation and notify all stakeholders. They should also have a few available selectors and change keys one at a time to protect legitimate emails from being rejected.
Conclusion
Even though introducing email authentication best practices might sound like a technician’s area of expertise, every email marketer should do that as they bear responsibility for the legitimacy of their digital correspondence and the safety of their customers in the channel.
If something goes awry, it will be their duty to solve the problem, mitigate its aftermath, and even face fines. By fortifying email channels with email authentication best practices, companies occupy a proactive position in their fight against cyber-attacks and in the pursuit of establishing a safe environment in their email channel.
Apart from fulfilling their part of accountability, introducing email authentication best practices comes with numerous benefits that empower companies to reach new heights of success. They enhance the deliverability rate, improve the sender’s reputation, avoid blacklisting and fines, build healthy, transparent, and reliable customer relationships, amplify the company’s credibility, and increase customer engagement that translates into high campaign ROI and revenue.
Finally, with SPF, DKIM, DMARC, ARC, and BIMI, companies get much-needed control over what is happening in email channels. Thanks to reports provided by DMARC, they get insights on how to fix issues and improve safety.
However, they still need to introduce extra measures for hardware and software in their servers and domains, like installing an advanced anti-malware solution or upgrading to the recent firewall version. Nevertheless, email authentication could be a solid foundation for creating a safe place for subscribers and ensuring mail providers and receiving servers that the company is a responsible, reliable, and legitimate player in the arena.