Email is the most popular channel of communication between the company and the target market. Therefore, it comes as no surprise that it is the prime target for hackers. According to recent studies, it is involved in more than 90% of all network attacks that cause tremendous financial loss for both organizations and customers.
To deescalate this situation and prevent phishing and spoofing, numerous companies have turned their heads to authentication protocols designed to address vulnerabilities of emails. We have already pondered the two most widespread and trusted standards on the web: SPF and DKIM. The time has come to understand what is DMARC record that enjoys the benefits of both these security technologies and even take them to the next level by providing tools for getting feedback on the email ecosystem.
So, what is DMARC, and why is it important for emails?
What is DMARC?
Before moving to the DMARC record and DMARC setup essentials, it is crucial to understand what is DMARC.
Domain-based Message Authentication, Reporting & Conformance, aka DMARC, is a free email authentication protocol. Its main goal is to safeguard the domain from being used in hacker attacks, including spoofing, phishing, and email scams.
As we have already noted, it is appeared due to a staggering level of cybercrimes. According to recent stats,
- more than 35% of all phishing attacks globally accounted for webmail services and Saas;
- every other company in the World was targeted by a ransomware attack last year;
- phishing attacks cause a quarter of all data breaches.
The great thing about DMARC is that it gets the most out of SPF and DKIM protocols and extends its mechanisms to make the authentication process accurate and effective. With DMARC, the owner of the domain formulates a policy using DNS records. He or she can specify such things as
- what domains have permission to send emails on behalf of the organization;
- what keys to use to sign and validate emails;
- what ISPs should do with emails that were not originated from authorized domains or fail the DKIM test and the DMARC test.
That is not all. The most significant advantage of DMARC is that, unlike SPF and DKIM, it is a reporting specification. With DMARC in place, the receiving mail server can send back a report about messages that fail. It is available in two formats: aggregate report and forensic report.
Simply put, the aggregate reports include information about the “report domain” and XML file with emails that failed verification. Forensic reports are failure reports that include details of messages that fail SPF, DKIM, or both. Together they offer insight into how your email moves through the ecosystem and what units use your email domain.
To sum up.
DMARC does three essential things:
- Verify email messages to be authenticated and legitimate.
- Provide instructions on what to do with illegitimate email messages.
- Generate reports and send them back so that the sender can fight spoofing on its side.
Due to such an extending authentication mechanism, most ISPs find DMARC quite an effective protocol and use it to determine the authenticity of the email sender. Based on DMARC results, ISPs decide whether the email will pass all the barriers and get to the inbox, whether it will be put into a junk folder or rejected and reported as a malicious threat.
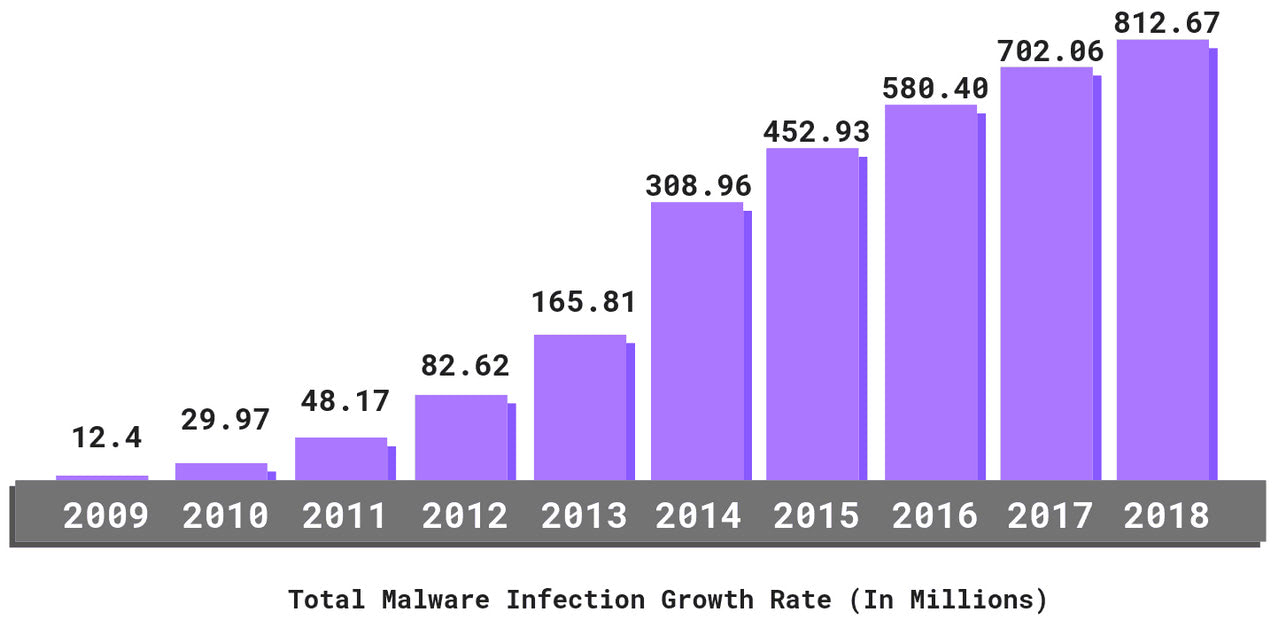
Malware Infection Growth Rate by Purplesec
What is DMARC Record?
DMARC record is the heart and soul of DMARC security standard. It is a DNS TXT Record that gives instructions to receiving mail server (ISPs, Gmail, Yahoo, etc.) about what should be done with the messages after checking SPF and DKIM records and DMARC test. It has three main policies:
- None. Monitors traffic without further actions.
- Quarantine. Send messages that fail DMARC to the junk folder.
- Reject. Turn down all unauthorized emails.
If no DMARC record is in place, the receiving side draws its own conclusion about what to do with that.
It should also be noted that even if the email passes the DMARC check, it can still be rejected because ISPs consider other factors. For example, if the sender’s IP address is blacklisted, all its messages will be rejected, regardless of DMARC.
What is Inside DMARC Record?
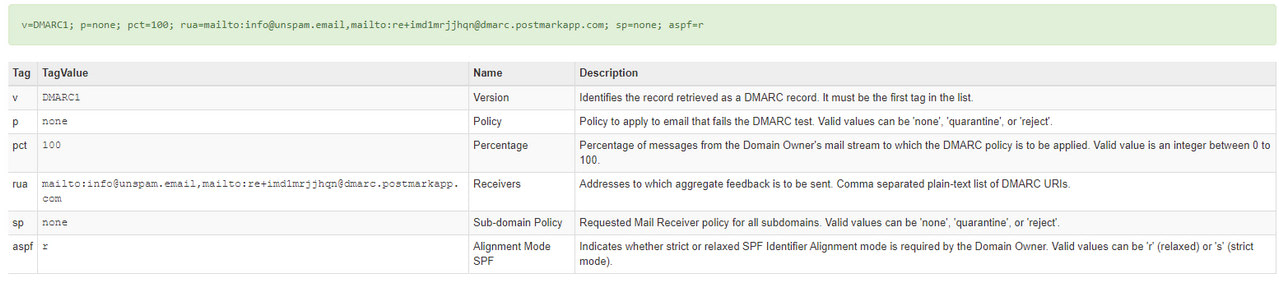
DMARC record is a modified DNS TXT record. It adheres to a particular format and syntax and is made of tags with name and corresponding value. There are required and optional tags. Let us consider the most popular ones:
- “v” indicates a version of the DMARC protocol. As a rule, it is “DMARC1”. It is a must-have for DMARC setup since if it is not specified, the receiving side will skip the DMARC check-up.
- “p” indicates policy. It comes in three options:
- None. It means doing nothing with fail messages.
- Quarantine. It means putting failed messages in the spam folder.
- Reject. It means blocking all failed messages.
- “sp” indicates policy for the subdomain. Note, you can have different policies for the main domain and subdomains. It is also important to note that the subdomain can also publish its DMARC record. It will be checked before the main domain.
- “pct” indicates a percentage of “failed” emails on which apply the policy.
- “rua” tells where to send reports about the messages. You can add multiple reporting addresses.
- “adkim=” indicates the type of “alignment test.” It has two options: “s” for strict and “r” for relaxed.
The regular DMARC record looks like this:
v=DMARC1; p=reject; rua=mailto:dmarc_reports@your_domain_name.com
The vital thing to note, DMARC can override the policy specified in DKIM. It comes in handy in numerous everyday situations. For example, the sender wants to implement the policy not to all messages but only to a certain percentage; or the letter arrived from a trusted source, so it should go straight to the inbox.
How Does DMARC Work?
The first thing to understand about DMARC working flow is that at least one authentication protocol (SPF or DKIM) should be enforced. Also, the DMARC record has to be set up.
The working flow behind DMARC is pretty simple and straightforward similar to SPF and DKIM. Let us walk through its key stages:
- Step 1 – After receiving the email, the mail server checks if there’s an existing DMARC record.
- Step 2 – If the DMARC record is found, the server initiates SPF and DKIM protocols to test the email on legitimacy and define whether the domain has the right to send emails on behalf of the sender and/or the email is signed.
- Step 3 – After SPF and DKIM tests, the server initiates an “alignment test” to verify such vital things as:
- whether the “<From:>” domain matches the “return-path” domain, in case SPF is in place;
- whether the sender’s domain matches the domain an email was sent from, if DKIM is in place.
The alignment requirements come in two versions.
- The first one is strict. It means that domains need precisely match.
- The second one is “relaxed.” It means that only base domains need to match precisely, allowing for different subdomains.
- Step 4 – The receiving side defines whether the DMARC check is successful or not. The DMARC test considers successful if the authentication protocol (either SPF or DKIM) is successful and its corresponding “alignment test” is also successful.
- If the DMARC test is successful, the receiving server may let the email in.
- If the DMARC test fails, then receiving server retrieves instructions for failed messages from DMARC records.
- Step 5 – The receiving mail server generates a report and sends it back. It includes DMARC verification results and aggregated data about failing checks.
Note that even though DMARC is a highly regarded authentication protocol, it still does not mean that ISPs will follow its instructions without reservation. ISPs consider numerous factors before drawing the final decision. However, DMARC sends a strong signal to the receiving server about the fate of the message.
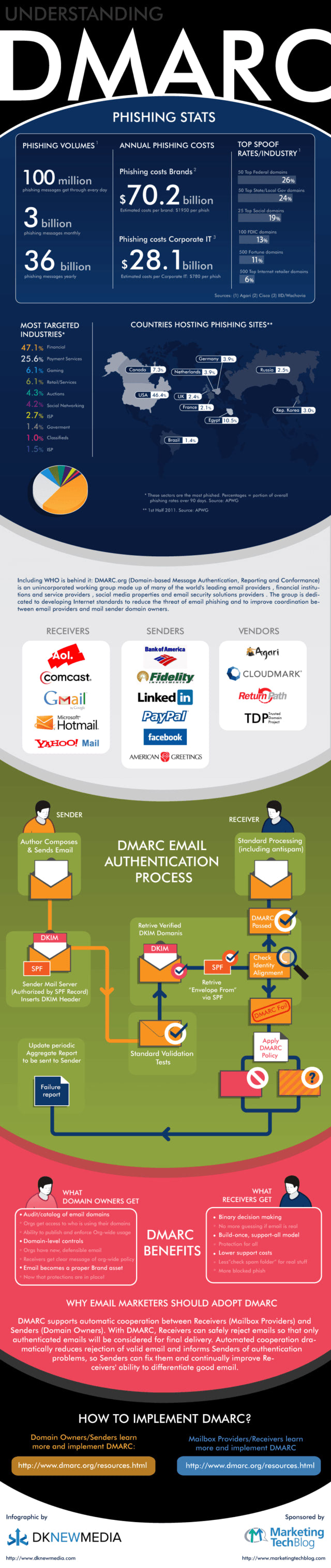
DMARC Infographic
Flaws of DMARC Record
DMARC has been proven highly effective; however, it still suffers some shortcomings. Let us consider the most obvious ones:
- DMARC setup does not fight all phishing attacks. Initially, it was designed to block direct spoofing.
- DMARC setup cannot battle cousin domain attacks, nor does it display name abuse.
- DMARC can still be considered successful if one of the authentication protocols fails. For example, SPF and its “alignment test” fail, but DKIM and its corresponding “alignment test” succeed – in this case, DMARC still considers successful.
- DMARC can be difficult to set up on your own. It is highly recommended to use wizards because even the tiniest mistakes in configuration may lead to drastic outcomes.
- DMARC was not created for the cloud era; therefore, those companies that use cloud services may suffer limitations.
- DMARC setup is not very easy to manage, even though it is simple in principle. For instance, you need a special tool to analyze reports because they are created for machines, not humans.
There are not too many limitations to DMARC. The majority of them could be downsided. However, it is important to remember that DMARC also includes some shortcomings of SPF and DKIM since it is based on these protocols. Therefore, to create overall protection, you need to plug in all loopholes.
Why is DMARC Record Important for Email?
Despite the shortcomings that the DMARC record has, it still brings benefits to the organizations. Deploying this authentication protocol is increasingly important because of these advantages:
- With DMARC setup, Internet Service Providers efficiently fight malicious email practices.
- DMARC setup saves customers from the invasion of malicious newsletters or viruses.
- DMARC setup helps ISPs better identify hackers.
- DMARC provides an authentication report to create a transparent connection between the company and end-user by showing who is sending email from the owner’s domain.
- DMARC records help to minimize false positives.
- DMARC fights unauthorized use of your email domain.
- DMARC record takes reputation to the next level. This involves improving your sender’s reputation and brand reputation, making your company’s position strong in the market.
- DMARC setup makes the whole email ecosystem more secure and trustworthy.
- DMARC improves email deliverability rates that play a crucial role in achieving the proper level of open rates and conversion rates.
How to Set up DMARC Record?
To set up a DMARC record, you need to undertake several necessary steps. Let us walk through them
Step 1 – Deploy SPF and DKIM.
If SPF and DKIM are in place for some time, then you can move to step 2. If you have just enforced these standards, then you need to wait at least 48 hours. This delay is necessary for changes in DNS to take effect.
Note, it is possible to define a DMARC record without SPF and DKIM; however, it is not recommended because DMARC will not do anything in this case. It will be pointless.
Also, it is vital to check SPF and DKIM to ensure that they work as intended.
Step 2 – Create a DMARC Record.
There are two required tag-value pairs that every DMARC record should have: “v” (version) and “p” (policy). Everything else is optional.
As we have already noted, the “v” tag should be “DMARC1”. As for “p,” it is for you to decide what to do with emails that fail authentication. Choose from three options: none, quarantine, or reject.
Also, it is highly recommended to add the “rua” tag so that receiving server can send reports back.
At this point, the basic DMARC record may look like this:
v=DMARC1; p=none; rua=”mailto: reports@your_domain_name.com
If you want to extend this record, you are welcome to use other tags.
Step 3 – Add DMARC Record to the DNS
Every hosting provider offers a unique wizard that helps business owners to add DMARC records to DNS. You do not have to do everything by yourself. These wizards usually come with handy and intuitive interfaces to add DMARC records and even create one simply by choosing the necessary tags and entering corresponding values.
Follow this simple procedure:
- Log into your domain registrar.
- Find DNS settings in the control panel and click on the option to manage or configure them.
- Find the ‘Add a New Record’ option.
- Click on it and choose a ‘TXT’ record.
- Add there your DMARC record.
Step 4 – Wait Until Changes Come into Force.
Similar to SPF and DKIM, it takes up to 48 hours or even more (depending on your hosting provider) for the DMARC record to come into force.
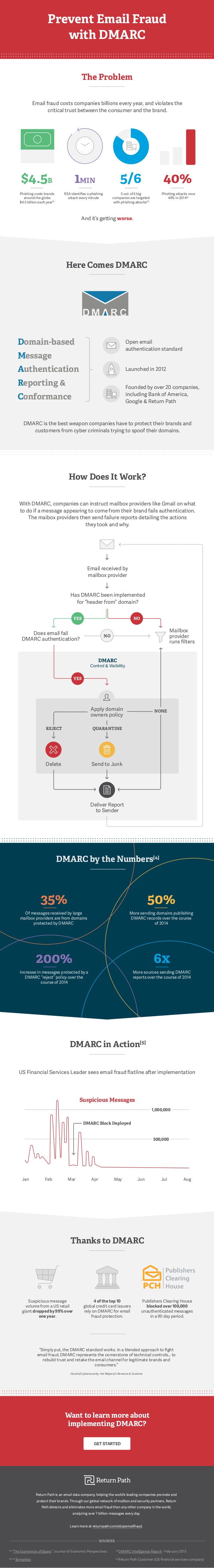
Prevent Email Fraud with DMARC Infographic
Step 5 – Validate DMARC Record
Much like with DKIM, when ISPs consider even the slightest mistake in syntax as a sign of fraud, error in DMARC record can be fatal. Therefore, it should be polished.
On top of that, setting up DMARC is just a beginning of a journey. It is crucial to test configuration for DMARC, SPF, and DKIM regularly to ensure that the defined policies do not block legitimate emails. Let us consider some good tools to check the DMARC record.
Tools to Check DMARC Record
Several popular tools check DMARC record on being valid:
- Unspam email. Unspam runs various tests on your email to provide an in-depth report about its health and efficiency. Here you can find details about your DMARC record and possible mistakes that you need to fix.
- DMARC Record Checker. The inspector checks whether the record is valid and whether it has mistakes in syntax.
- DMARC Check Tool. This DMARC record lookup runs a series of diagnostic tests, showing results in a handy tabular format.
- DMARC Record Lookup. This service does two things. First, it validates the record to ensure it works fine. Second, it generates a DMARC record based on your parameters.
- Phishing Scorecard Tool by Dmarcian. If you ever wonder who uses DMARC to find out whether domains of your beloved brands are phishing-proof, then this is a place to start your searches.
Let us consider some best practices for DMARC protection.
- Start with relaxed and quarantine options and only then work your way towards a strict regime.
- Use no more than two different destinations for reports because mailbox providers do not send reports to more than that.
- Do not list multiple RUA and RUF statements.
- If you have a big organization or numerous subdomains, it is better to use automated DMARC implementation since it helps to scale protocol efficiently.
- Use a special DMARC monitoring service to analyze the information because aggregate and forensic reports are machine-readable.
Conclusion
DMARC is one of the most powerful authentication protocols that has proven its validity and effectiveness through the years. It is not only about validating emails and rejecting those that are not authorized. It is about providing a way to coordinate the efforts of senders and receivers and put them in a strong position to fight spoofing and phishing attacks.
Even though DMARC is powerful tool, it is still a team player, not a loner. Being a representative of the layered approach, it should be combined with other security technologies to provide optimal protection and save companies from losing their money because of digital threats that cost businesses worldwide billions of dollars each year.